Is the Zoom App Safe to Use? An Overview of Its Security Flaws, Updates and Helpful Tips in Using It
qwikfone
December 11,2021
Is the Zoom App Safe to Use? An Overview of Its Security Flaws, Updates and Helpful Tips in Using It
by Ishaan Seth November 23, 2020
The Zoom app was the go to program for conferences ever since the pandemic hit. With businesses and schools closing down during the first few months, video conferences rose, and so was the demand for a platform that can host up to a hundred users easily. However, Zoom was plagued with numerous security issues that raised red flags. But with the company providing one Zoom security update after the other, can it be said that this program is already safe to use?
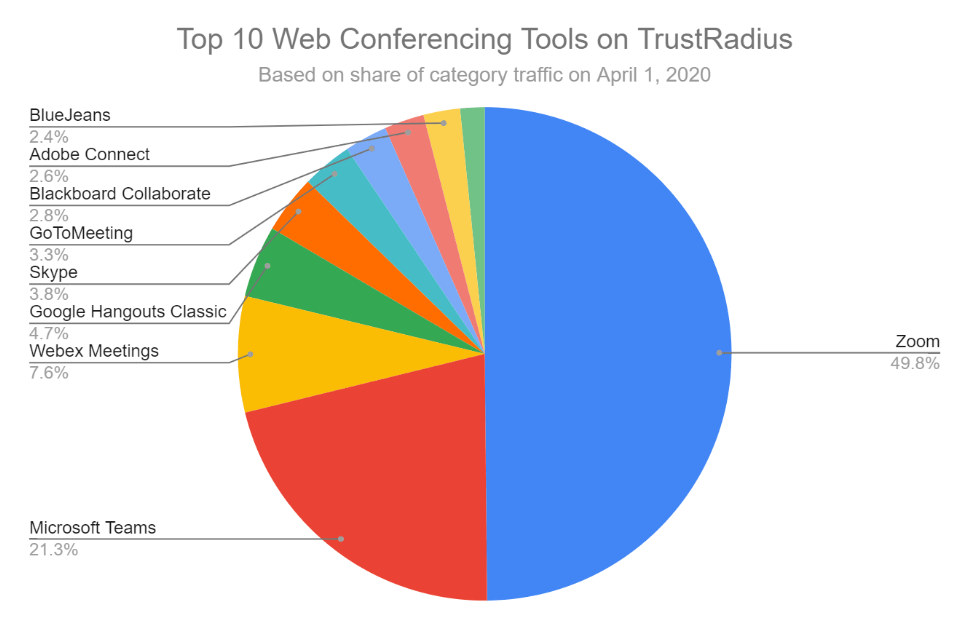
Zoom is the largest video conferencing platform (photo credit: TrustRadius)

Zoom’s Security Flaws
There were several security flaws that were found in this program during the first few months of its launch. As with any program, security is an important part of the software since it offers protection to the user. What are these flaws you ask?
Is the Zoom App Safe to Use? An Overview of Its Security Flaws, Updates and Helpful Tips in Using It

- Zoom Bombing.
During the first few months of the application, conferences were interrupted by random people who sent inappropriate content to the room. Although the host of the conference will be able to remove the said individuals, it was possible for them to come back using a different ID. - Missing End-to-End Encryption.
The lack of proper end-to-end encryption by Zoom had been questioned by many, especially those who are experts in security. Although the company stated that their end-to-end encryption was different from what other companies have, the problem was that the decryption was happening on the server side. This means that those who are running the network will be able to access files from the users.
However, the Federal Trade Commission stated recently that the company was actually misleading their users by engaging in deception with regards to the security of the platform. That said, Zoom is required to undergo reviews of their internal as well as external securities every two years. They are also required to have a program for managing vulnerabilities. It was also stipulated that Zoom should provide their customers with a two-step authentication which they are now doing. - Sneaky Installer.
Have you ever experienced a bug suddenly disrupting your computer’s function? Or that you found a program on your gadget that you did not install on your own? Well, it seems that the Zoom application can easily take over your own privileges on your gadget in order to install random software for suspicious purposes. This was called out by the experts as well as companies that were using the program too. - Email and Photo Leak.
Users of the program, such as Dutch users, found that their emails and photos were stored in a folder that is accessible to the public. For a platform with millions of users, this left their personal information vulnerable to anyone. This is a huge security leak and one that Zoom was tasked to fix.
The Latest on Zoom Security Update

The latest on Zoom security update (photo credit: techradar.com)
Zoom was given up to 90 days to address the security issues that it had. Now that the given deadline has passed, we had to ask what’s the latest on this program? According to Tom’s Guide, there were several updates that the company has made to its platform that fixed the previous issues that it had. Here are a few worth noting.
Combat Zoom Bombings
It appears that Zoom has finally made two features to address the issue of random people popping up in conferences to disrupt them. The company has issued two additional features that were designed to address this problem. The first one was referred to as “Suspend Participant Activities”. This feature puts the power on the host to pause the ongoing conference, remove those that were disrupting the activity, then resume after. The second feature was dubbed as “Report by Participants” where the members of the group call were able to report those who were disturbing the conference. Hopefully, these new add-ons will be able to make the video conferences more secure to the guests.
End-to-End Encryption
After months of silence from Zoom, the company announced in October that their end-to-end encryption will undergo beta testing in the third week of October. On October 27, the feature was finally launched but it was only limited to the Android platform since they had to wait for an approval from the tech giant, Apple.
This encryption feature was primarily for Zoom’s customers who paid for their subscription, but it appears that non-profit groups, such as in a school setting, may receive this feature since they are known. Is it possible that they will roll out this feature for those who are using the platform for free? It remains to be seen.
This encryption feature was primarily for Zoom’s customers who paid for their subscription, but it appears that non-profit groups, such as in a school setting, may receive this feature since they are known. Is it possible that they will roll out this feature for those who are using the platform for free? It remains to be seen.
Updated Security for Private Rooms in Zoom
A few months ago, the web interface of this video conferencing platform was down because it appeared that anyone can easily guess the six-digit PINs for these rooms by anyone. This was one of the reasons why many were able to bomb private conferences easily. Tom Anthony, a security researcher from Britain, wrote about how he was able to crash a Zoom conference within half an hour. The good news is that this was already fixed which is one less problem to worry about in this platform.
Zoom Security Tips to Consider for Safe Zoom Usage
A Zoom meeting underway (photo credit: theguardian.com)
With the latest Zoom security update in place, the question now is whether the application is finally safe to use by everyone. For the most part, this video conference platform is relatively safe to download and use, as long as you are not using it to talk about sensitive matters, such as your company’s secrets and such. This is still a good platform for virtual get-togethers especially during this pandemic. Even schools are enjoying this platform’s advantage of hosting up to a hundred people at the same time which other video conferencing programs have yet to achieve. If you still think that the alternative of zoom app for video conferencing can be found and better option then we can also have them easily online.
But after all that is said and done, it still pays to be more aware of your personal security when using this platform. As a matter of fact, there are several Zoom security best practices that you should follow such as:
But after all that is said and done, it still pays to be more aware of your personal security when using this platform. As a matter of fact, there are several Zoom security best practices that you should follow such as:
- Use a web browser when joining meetings. Instead of downloading the Zoom software for desktop, it is best that you open it from the web browser. One reason behind this is this version typically receives updates or enhancements faster compared to the desktop platform. According to Kaspersky, the browser version of Zoom doesn’t require permissions unlike when installing the platform directly into your device. This means that it is less vulnerable to Zoom security issues. When you join a meeting via a link, there will be a new tab that will be opened where you will be prompted to install the software. Check the fine print and locate the link where you can join through your choice of browser.
- Use password. Another example of Zoom security tips is to have your guests sign in using a password. This is applicable if you will be the host of a private conference to avoid being rudely interrupted by unknown individuals. This way, you won’t have to deal with the constant Zoom bombing that plagued users during the first few months of using this new online video conferencing platform.
- Set up authentication. The two-step authentication was finally rolled out by Zoom to help make their customers’ account more secure. If these Zoom security settings are activated, it will be difficult for potential hackers to get into your personal accounts even if they do have your addresses for your emails as well as passwords. This authentication process will have to pass a second layer of authentication such as a smartphone to be able to open the account. More of this will be discussed below.
Although the concept of Zoom was a great idea, especially since it allows a hundred users to converge in a single room virtually, it was prone to getting hacked in various ways. There have been reports already that these hackers have already created fake domains that are related to Zoom plus malware for the program too.
On a good note, if the company behind Zoom is able to find these flaws and address them as quickly as possible, there is a good chance that they will be able to keep their platform safe and secure for its users.
On a good note, if the company behind Zoom is able to find these flaws and address them as quickly as possible, there is a good chance that they will be able to keep their platform safe and secure for its users.
Setting Up the Zoom Two-Factor Authentication System
If this is your first time to set this up, you will need two things: your laptop or your desktop and your smartphone. See to it that the authenticator program is already installed in your device before you proceed.
Here are the steps you will need to follow:
Here are the steps you will need to follow:
- Sign in into your account via the web browser on your desktop.
- On the upper right portion of your monitor select My Account.
- Choose Profile which you will find on the left portion of your navigation bar.
- Select the Two-Factor Authentication which you will find almost at the end of your screen to activate it.
You will then have to decide what your second layer of authentication will be. Will it be via SMS, an Authentication program, or you can use both.
Via Authentication Application
Like it was mentioned before, you will need to ensure that you have your authenticator application already downloaded and installed on your mobile device, regardless of whether it is brand-new or refurbished, before you proceed with the authentication process. Once done, you can do the following:
- Choose the Authentication App on your profile page then input your password.
- You will have to create a new entry in the authenticator program in your mobile device.
- Move your smartphone’s camera towards the QR code that will appear on the web page of Zoom on your computer.
- You will need to input the temporary code provided by the authenticator program on your device to your computer to complete the registration.
Setting up Mobile Number
It does pay to have a multiple authentication process to go through especially with platforms such as Zoom where there is the danger of getting hacked into. To set up your mobile number for Zoom, you will need to do these steps:
- Choose SMS then proceed with typing your password for Zoom.
- You should then input your mobile number as well as the country code.
- You will receive a temporary code again which consists of six numbers. These numbers must be typed on the web page in your computer.
Zoom Security Still Needs a Lot of Work
Zoom is a promising video conferencing platform, there is no doubt about that. The very idea of being able to connect to multiple individuals without the program crashing is exceptional already. After all, video conferencing applications such as Facebook, Skype, and Google’s Hangouts have limited capacity. In these times when social distancing is being practiced and many are working from home, Zoom really does shine the most.
However, the security flaws that it has is disconcerting, especially when previous reports have stated that anyone can easily enter a conference to drop unwanted GIFs, or send malwares via links in the chat room. Although the company is trying their best to fix the problem one by one via a Zoom security update, there is still much to do to make this platform a secure space for everyone. Even when you buy refurbished phones UK from sites like QwikFone to use for Zoom alone, you will still need to follow the Zoom security best practices as much as possible for your own safety.
It may take some time before we see all the flaws in Zoom to be corrected, but on a good note, they are amenable to making these changes based on customer feedback and the reviews of the security experts.
Is this platform safe? For regular video get-togethers and online learning, this application may work just fine. However, for businesses or high-profile gatherings where sensitive information needs to be discussed, you might want to look for other options instead. Even with the multiple authentication system that Zoom has rolled out for added security, it would be better to try a more secure system that has been developed by trusted brands like Microsoft and Google.
However, the security flaws that it has is disconcerting, especially when previous reports have stated that anyone can easily enter a conference to drop unwanted GIFs, or send malwares via links in the chat room. Although the company is trying their best to fix the problem one by one via a Zoom security update, there is still much to do to make this platform a secure space for everyone. Even when you buy refurbished phones UK from sites like QwikFone to use for Zoom alone, you will still need to follow the Zoom security best practices as much as possible for your own safety.
It may take some time before we see all the flaws in Zoom to be corrected, but on a good note, they are amenable to making these changes based on customer feedback and the reviews of the security experts.
Is this platform safe? For regular video get-togethers and online learning, this application may work just fine. However, for businesses or high-profile gatherings where sensitive information needs to be discussed, you might want to look for other options instead. Even with the multiple authentication system that Zoom has rolled out for added security, it would be better to try a more secure system that has been developed by trusted brands like Microsoft and Google.
